Someone found an “easy peasy” vulnerability in the Safemoon token pair and made off with almost 9 million dollars.
No big deal, right? Just another reminder to double-check your smart contract security before you lose millions of dollars.
Summary:
On March 28, 2023, an attacker exploited an access control vulnerability in the burn() function of the Safemoon smart contract. The vulnerability was introduced when the SafeMoon Deployer address upgraded the token contract to a new implementation. The attack resulted in a loss of around 8.9 million.
About Safemoon:
The Safemoon protocol is a decentralized finance (DeFi) platform built on the Binance Smart Chain. It aims to provide a safe and secure platform for users to trade and hold cryptocurrencies. The platform includes features such as static rewards, automatic LP (liquidity provider) acquisition, and a token burn mechanism.
On-Chain Details:
MEV Bot Address: 0x286e09932b8d096cba3423d12965042736b8f850
Attacker EOA: 0x97226254fF489f3257E68222F184Ac2b6E20A4ff
Safemoon Deployer’s EOA: 0x678ee23173dce625a90ed651e91ca5138149f590
Original attack txn (failed): 0xbcf5e30c164837b5d7c42fd7e33e47a0072dc014e7f0a67aa7710af49d0ce53b
MEV Bot Attack txn: 0x48e52a12cb297354a2a1c54cbc897cf3772328e7e71f51c9889bb8c5e533a934
Root Cause:
The root cause of the attack was that during an upgrade of the Safe Moon contract, an access control vulnerability was introduced in the burn function. This vulnerability allowed an attacker to burn tokens from any address. Vulnerable code can be found here.

How did the attack occur?
- The attacker started by purchasing around 102 WBNB tokens before exchanging them for their SFM pair counterpart.
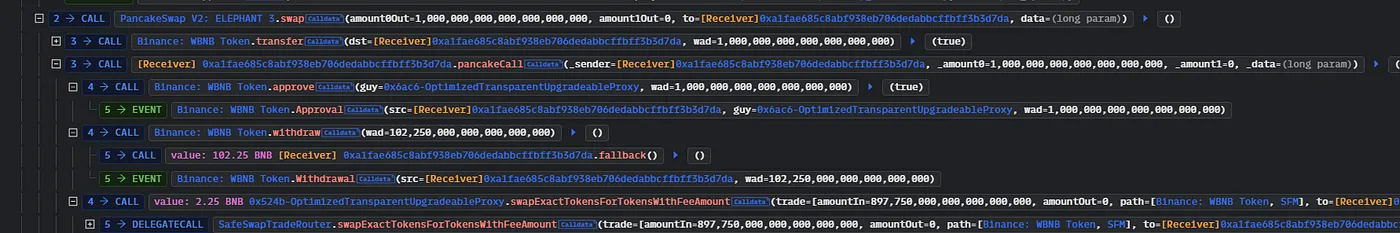
- Now that the burn() function was public, the attacker then burned a huge number of SFM tokens, inflating the price of SFM tokens.
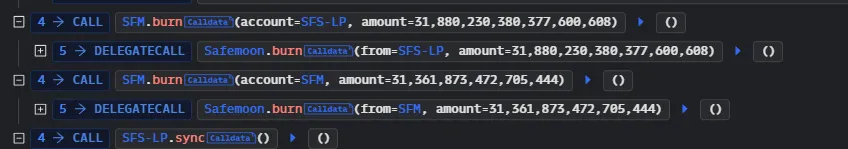
- Finally, the attacker converted the SFM tokens to their WBNB counterpart and withdrew around $8.9 million in tokens, resulting in a massive loss for SafeMoon users.

The Story Turns:
An MEV bot front-ran the original attack transaction. The same MEV bot was involved in the Nuwa Exploiter and DBALL Exploiter hacks.
After the Exploit:
The team announced the attack on their Twitter account. They further stated that it had affected the SFM:BNB LP pool, but the DEX was safe.
Mar-29–2023: The exploiter has indicated that they are currently waiting for a secure communication channel in order to return the funds to the team in a transaction.
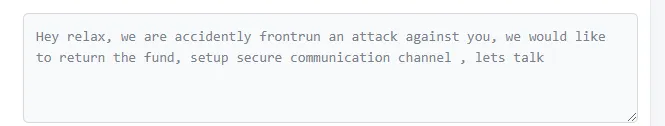
Mar-30–2023: Safemoon Replied that the attacker can return funds to Safemoon's Treasury:

How Could this attack have been prevented?
The project should have conducted a comprehensive audit and double-checked the security of your smart contract. To minimize DeFi protocol attacks, implement strict security standards, despite imperfect measures. Third-party auditors must routinely assess smart contracts, identify vulnerabilities, and propose mitigation plans.



All Comments